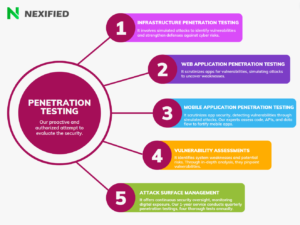
In today’s digital landscape, asset security has emerged as a cornerstone of cyber security, underscoring the importance of robust management and protection of capital assets. Leveraging security assessments and rigorous testing, organizations can bolster their defenses against evolving cyber threats, safeguarding their network assets and ensuring resilient risk management strategies.
This article will explore the critical role of asset testing in enhancing an organization’s cyber security posture, from preventing data breaches to the broad spectrum of benefits it offers. Through comprehensive analysis and industry-specific insights, readers will gain a deeper understanding of why asset security testing should be a top priority for every organization.
The Critical Role of Asset Security Testing in Cybersecurity
Asset management, particularly in cybersecurity, is a linchpin for financial institutions and organizations across various sectors. This practice is multifaceted, encompassing the identification, tracking, and management of all network assets to ensure security and compliance. Here’s a breakdown of its critical components:
- Risk Assessment and Management: Proper asset management underpins risk assessment by identifying vulnerabilities and implementing access control measures. It plays a pivotal role in incident response and achieving regulatory compliance, thereby fortifying an organization’s cybersecurity posture.
- IT Asset Management (ITAM): ITAM provides real-time insight into a firm’s assets, aiding in vulnerability management, compliance tasks, and enhancing incident response. It’s crucial for updating asset inventory, aligning with security standards like CIS Top 20, HIPAA, and PCI.
- Asset Inventories: An accurate and current asset inventory aids organizations in aligning their assets with business objectives and risk strategies. It is crucial for effective risk management, allowing for the tracking, auditing, and risk assessment of inventory. An overlooked aspect of asset inventories is their scalability; as companies grow, maintaining an organized inventory becomes challenging but essential for managing and mitigating risks effectively.
Asset testing is crucial in cybersecurity, providing a strong security framework through comprehensive asset accounting, vulnerability identification and mitigation, and compliance adherence.
Benefits of Cybersecurity Asset Security Testing
Organizations globally allocate between 10-12% of their IT budgets to cyber security, underscoring the pivotal role of Cybersecurity Asset Management (CSAM) in safeguarding IT assets. CSAM extends its benefits across various dimensions:
- Real-time Visibility and Control: CSAM tools aggregate asset data into a single dashboard, offering real-time visibility that enables swift, informed decision-making. The comprehensive view facilitates the detection of threats before they escalate, ensuring that we can quickly identify and address unpatched vulnerabilities and malicious activities.
- Enhanced Compliance and Security Posture: By assessing assets against specific environments and security standards, CSAM provides insights into asset inventory, configuration, and compliance, aiding in the identification and secure disposal of end-of-life IT assets. This not only ensures compliance with regulations but also strengthens the organization’s overall security posture.
- Proactive Incident Management and Cost Efficiency: CSAM prioritizes incident management efforts based on risk and ROI, allowing IT teams to focus on protecting high-priority assets. This strategic approach to asset management not only enhances security but also optimizes resource allocation, contributing to overall cost efficiency.
Integrating CSAM into a business’s cybersecurity plan provides a comprehensive asset security solution, improving compliance, visibility, incident response, and resource distribution.
Preventing Data Breaches Through Asset Security Testing
Preventing data breaches requires a proactive approach to asset security, where understanding and prioritizing the significance of assets becomes paramount. Triaxiom Security’s suite of services, including Penetration Testing, Compliance Audit, and Strategic Consulting, plays a crucial role in this process. These services help organizations identify vulnerabilities, meet security standards, and enhance their security posture.
Key Steps in Asset Testing for Data Breach Prevention:
- Risk Assessment Focused on Specific Needs: Traditional risk assessments often fail to account for an organization’s unique business context. A more tailored approach, focusing on vulnerabilities, misconfigurations, and security issues specific to the organization, is essential.
- Asset Importance Ranking:
- Be Organization-Focused: Prioritize assets based on their importance to the organization, not their global significance.
- Multi-Factor Analysis: Employ a comprehensive analysis considering various factors to accurately determine an asset’s importance level.
- Total Visibility: Achieve up-to-date visibility of the attack surface to fine-tune importance ranking.
- Understanding Cyber Risk Prioritization Challenges: The complexity and breadth of an organization’s attack surface can make cyber risk prioritization daunting. However, by focusing on the critical areas identified through asset importance ranking, organizations can strategically direct their remediation efforts.
This focused approach to asset testing and prioritization aids in significantly reducing the risk of data breaches, which can have devastating operational, financial, and reputational impacts. Learn what is Data Breach
Conclusion
It has become apparent that maintaining and enhancing an organization’s cybersecurity posture through rigorous asset testing has incredibly high stakes. From fortifying defenses against cyber threats to ensuring compliance and optimizing incident management, the benefits of a well-executed Cybersecurity Asset Management (CSAM) approach are manifold. Organizations that prioritize these strategies not only bolster their security but also pave the way for more efficient resource allocation and cost savings, proving that the investment in asset testing is both a protective measure and a strategic business decision.
Nevertheless, the complexity of the digital landscape and the ever-evolving nature of cyber threats require organizations to remain proactive and vigilant. The call to action for businesses is clear: to stay ahead of potential vulnerabilities and ensure the integrity of their critical assets. For those seeking to enhance their cybersecurity measures, the opportunity to Contact Us for services provides a crucial first step towards safeguarding their digital terrain. Embracing this proactive stance is not just about preventing data breaches; it’s about securing the future of the organization in an increasingly digital world.
FAQs
Q: What is the process for determining which assets are most vital to an organization?
A: To determine the most critical assets, you should start by identifying the key business functions dependent on these assets, such as production, supply chain management, customer service, and finance. This helps in understanding which assets bear the most business risk.
Q: What is the rationale behind prioritizing assets and associated risks?
A: The main goal of prioritizing assets and risks is to create a ranking from the most to the least critical risks. The strategic allocation of resources effectively supports the organization’s mission and business needs, with this ranking serving as its foundation.
Q: How does asset security contribute to an organization’s overall well-being?
A: Asset security is crucial because it forms the core of a security program, enhancing the organization’s security posture and enabling businesses to mitigate risks and ensure that their operations are not disrupted.
Q: Why is it essential for organizations to identify assets during a risk assessment?
A: Identifying IT assets is a fundamental step in conducting a cybersecurity risk assessment. By creating an asset register, an organization can clearly understand what assets are valuable and designate responsibility for their protection, which is vital for maintaining security.