In the ever-evolving cyberspace, the paramount concern has become the need for robust cybersecurity measures. Penetration Testing (Pen Testing), a security practice, plays a critical role in strengthening the Secure Software Development Life Cycle (SSDLC). Pen Testing identifies vulnerabilities and security weaknesses, providing valuable insights and enabling organizations to significantly improve their security posture.

Understanding Penetration Testing for SSDLC
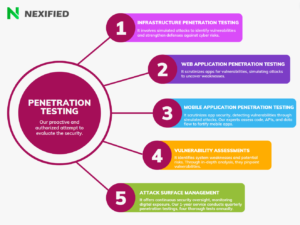
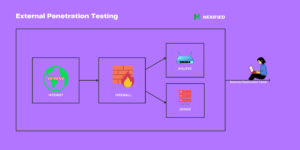
Cybersecurity professionals proactively use Penetration Testing as a measure, which involves conducting authorized simulated attacks on a system to evaluate its security. It serves as a critical aspect of the SSDLC, unearthing vulnerabilities, validating existing security controls, and ensuring software resilience against potential cyber attacks.
The Essence of Penetration Testing
In the cybersecurity sphere, people deem Pen Testing as a best practice. It not only discovers application security defects but also gauges the health of an organization’s SSDLC. Regulatory bodies often mandate Automated Pen Tests, which require minimal tooling or training from the customer and are considerably thorough in pinpointing security flaws.
Human Element in Penetration Testing
Automated Pen Tests, despite their efficiency, cannot replace the human element in Pen Testing execution. Human pen testers, who can mimic human hackers, excel at evaluating an application’s response to a Pen Test and have the potential to catch responses that automated software might overlook.
Penetration Testing: A Catalyst for SDLC Improvement
You can leverage Pen Testing, typically seen as a defect discovery tool, to identify inflection points in your SDLC where you can prevent vulnerabilities. This change in use can greatly improve the human and financial efficiency of Pen Testing.
Pen Testing as a SDLC Diagnostic Tool
Instead of merely relying on Pen Tests for defect detection, organizations can perform a blameless postmortem using them, analyzing whether they need improvements to recognize potential failures at specific points in the SDLC.
Pen Testing for Process Improvement
You can re-position Penetration Testing to find those inflection points in your SDLC where you can prevent vulnerabilities. If you use Pen Testing for this purpose, you’re utilizing the human and financial costs of Pen Testing more efficiently than just focusing on defect discovery. Pen Testing can assist you in detecting the processes in your SDLC that let vulnerabilities creep in. Therefore, if you start fixing those processes, you’ll also reduce future vulnerabilities.
Leveraging Pen Testing for SSDLC
You can utilize Pen Testing results in various ways for Secure Software Development Life Cycle (SSDLC). Here are a few strategies:
Policy and Standards Revision
Actively update your policy and standards to state outright that we do not tolerate production defects. Allocate funds for training, tooling, and making defect detection and remediation a priority. Let senior leadership give approval for and enforce changes to policy and standards based on Pen Test results.
Requirements Formulation
Start writing reusable, implementable, and testable security requirements that address the OWASP Top 10 vulnerabilities. When Pen Tests detect security defects, write user stories and approval criteria to prevent those defects.
Employee Training
Detect a security fault with your Pen Tests and determine if your training’s learning objectives cover this issue. If the training program does not train developers to prevent security flaws, then it failed, not the development team.
Threat Modeling and Design Review
By proactively finding and preventing whole classes of problems, you can improve the design. Use your Pen Testing results to modify threat modeling checklists, covering design decisions that could prevent or mitigate security faults. Establish secure design patterns that allow developers to rule out entire classes of defects.
In-Band SDLC Flaw Discovery Tooling
Instead of relying on Pen Testing, shift to in-band SDLC flaw discovery tooling to discover and remediate entire classes of flaws.
Static and Dynamic Application Security Testing
You can use static AST or code review checklists to prevent industry-known vulnerabilities that naïve developers miss. At the same time, you can use dynamic application security testing (DAST) or interactive application security testing (IAST) to discover runtime bugs and setup concerns that Pen Tests typically disclose.
Quality Assurance-Based Security Tests
Alternatively, instead of using Pen Tests, you can use QA-based security tests to uncover edge cases and logic flaws that scanning rule sets miss.
Production Risk Management
After Pen Testing detects flaws, you need to build gating mechanisms to catch and stop them from moving down the SDLC.
The Future of Penetration Testing
Once we have addressed all these vulnerability issues, we can start repositioning Pen Testing in the risk management portfolio. We need to rethink the way we use Pen Tests in risk management. The human-driven nature of the Pen Test ensures a thorough examination of underutilized capabilities. When we incorporate Pen Test results into our SDLC, we use the results to prioritize recommendations. However, Pen Testing cannot provide direct evidence for training needs, compliance enforcement, vulnerability management needs, security champions, or other key capabilities that do not directly prevent or detect Pen Test security defects. Additionally, it’s important to understand that Pen Testing plays a critical role within a broader cybersecurity framework.
Conclusion
Penetration Testing doesn’t just discover defects anymore; it has evolved into a powerful diagnostic tool for the SSDLC. When organizations shift their perspective on how they use Pen Testing, they can uncover valuable insights into their development processes. This leads to improved security, increased cost-effectiveness, and, moreover, enhanced customer trust.
Great info, thanks for sharing. Please check the email for work