Penetration testing or ethical hacking is vital for robust cybersecurity as it proactively identifies vulnerabilities that may cause future attacks. As organizations manage sensitive data, safeguarding software from internal and external threats is crucial to maintain legal compliance and business integrity. Understanding the distinction between external and internal penetration testing, each with unique scope, methodology, and purpose, strengthens defenses against various cyber threats.
External penetration tests concentrate on securing your organization’s external-facing assets like websites and external network services, while the design of internal tests aims to evaluate the potential results of an insider attack. These tests identify ways to exploit internal data dependencies and systems. The distinction between external vs internal and internal vs external testing illuminates how each method addresses different aspects of your organization’s security posture. This article aims to clarify the key differences between external and internal penetration testing, highlighting their strategic importance and guiding you on implementing both to ensure comprehensive protection from all types of cyber threats.
What is Penetration Testing?
Penetration testing, commonly referred to as pen testing or ethical hacking, is a vital cybersecurity technique. It serves as a proactive measure, allowing organizations to identify, test, and highlight vulnerabilities within their security posture. This process is not a one-off event; rather, it involves consistent, self-initiated improvements based on the test reports generated.
We can break down the methodology behind pen testing into six distinct stages:
- Reconnaissance and Planning: Gathering information to prepare for the attack simulation.
- Scanning: Understanding how the target application responds to various intrusion attempts.
- Obtaining Entry: Breaching the system using vulnerabilities found during the scanning phase.
- Maintaining Access: Seeing if we can use the vulnerability to maintain access and achieve a persistent presence in the exploited system.
- Analysis: Evaluating and documenting the vulnerabilities, the data accessed, and the time the tester was able to remain in the system undetected.
- Cleanup and Remediation: Restoring the systems to pre-test states and addressing vulnerabilities.
Ethical hackers and IT professionals execute pen testing, using hacking techniques to help companies identify potential entry points into their infrastructure. These experts simulate cyber-attacks under controlled conditions to uncover any weak spots in a system’s defenses which attackers could exploit. The process includes using software for brute-force attacks or SQL injections and hardware specifically designed for pen testing. Upon completion, ethical hackers share their findings with the target company’s security team, providing insights into the system’s vulnerabilities and suggesting improvements.
This cybersecurity exercise is critical for risk assessment, security awareness, reputation protection, and compliance. It’s a part of a holistic web application security strategy, often conducted by third-party security experts to ensure an unbiased evaluation from a hacker’s perspective. Cybersecurity experts recommend regular penetration testing to defend against the increasing threat of cyberattacks. This testing supports regulatory compliance and examines both physical security measures and potential security weaknesses in people, known as social testing.
External Penetration Testing: Scope and Methodology
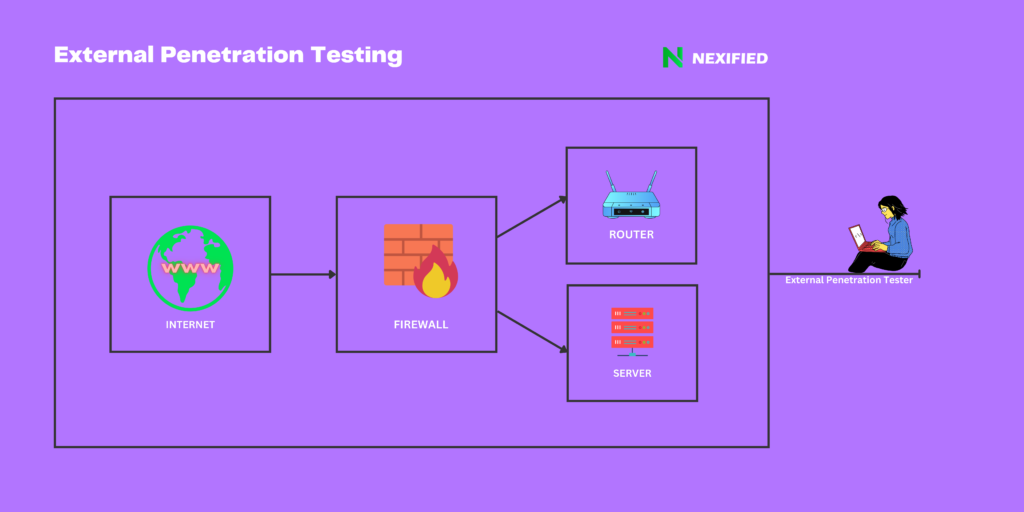
External penetration testing is crucial for organizations to protect their outward-facing assets from cyber threats. This process imitates real threat actors, aiming to exploit vulnerabilities externally without proper access.
Methodology Overview:
- Planning and Reconnaissance: Initially, we define the scope of engagement, which includes IP addresses/ranges, domains, subdomains, and cloud assets. This phase also establishes the Rules of Engagement (RoE), setting clear objectives, timelines, and communication protocols.
- Execution: Involves both passive and active reconnaissance to gather information about the target. We follow this with vulnerability scans using tools like Nessus, then manually test and exploit to identify and exploit vulnerabilities.
- Post-Execution: Concludes with a comprehensive report and debriefing, detailing the findings, exploited vulnerabilities, and recommendations for bolstering security.
Our structured method for external penetration testing identifies vulnerabilities and offers actionable steps to strengthen your defense against potential threats.
Internal Penetration Testing: Scope and Methodology
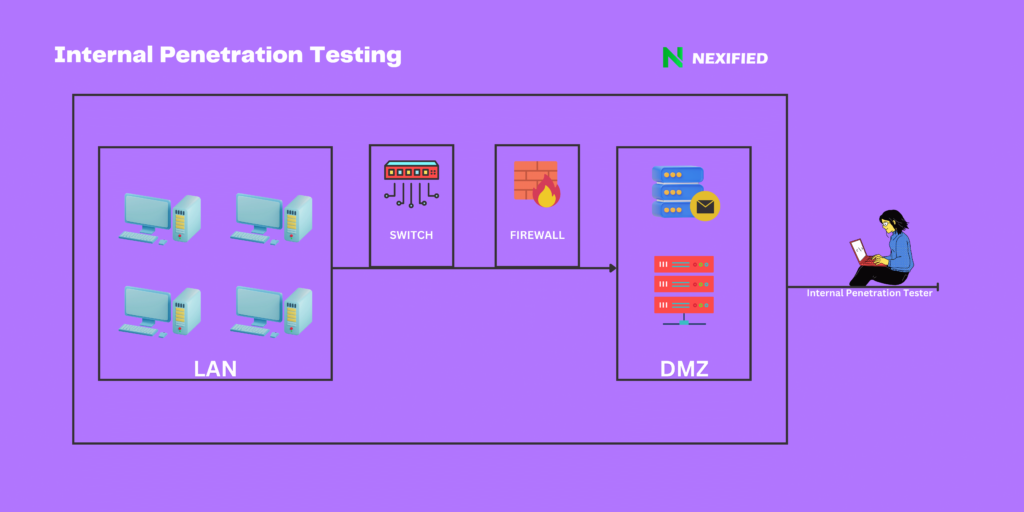
Let’s delve into the realm of Internal Penetration Testing, a crucial element in safeguarding an institution’s internal network against potential hazards.
Methodology Overview:
- Initial Phase:
- Information Gathering: Identifies targets within the organization such as servers, workstations, and network equipment.
- Scope Definition: Based on the number of live hosts on the internal network.
- Testing Procedures:
- Internal Network Scans: To detect known Trojans and assess third-party security configurations.
- Vulnerability Identification and Exploitation: Includes port scanning, system fingerprinting, and manual vulnerability testing.
- Security Controls Assessment: Evaluates firewalls, IDS/IPS, and database security measures.
Objectives:
- Internal Threat Identification: Targets internal vulnerabilities and insider threats, including malicious insiders and insecure third-party vendors.
- Lateral Movement Analysis: Determines how far an attacker can move through the network, highlighting weaknesses in policy enforcement and secure system maintenance.
- Cost-Saving: Aims to uncover internal vulnerabilities before they result in costly data breaches.
Internal penetration testing, which evaluates potential exploits from within an organization, is crucial for a robust security posture. It complements external testing and effectively safeguards against internal and external threats.
Key Differences: External vs Internal Penetration Testing
Understanding the core differences between external and internal penetration testing is essential for tailoring your cybersecurity strategy effectively. Here, we break down the key distinctions:
- Perspective of Attack:
- External Penetration Testing actively simulates attacks from external threat actors who have no prior access, concentrating on potential vulnerabilities that outside forces could exploit.
- In Internal Penetration Testing, we assume that a potential attacker, possibly a disgruntled employee, has internal access and we aim to identify the potential damage they could cause from within.
- Areas of Focus:
- External: Targets public networks and external-facing assets like web applications, focusing on administrative features and systems that could allow attackers to access sensitive data.
- Internal: Concentrates on internal networks, identifying insider threats and vulnerabilities within, including privilege escalation and credential stealing.
- Frequency and Cost:
- External Testing: Often outsourced and conducted a few times due to cost, focusing on evolving and common external threats.
- Internal Testing: Requires an in-house security team for more comprehensive, regular checks, despite internal threats being less common.
These distinctions underscore the importance of implementing both testing types for a robust cybersecurity posture, addressing both external and internal vulnerabilities.
Strategic Importance of Both Testing Types
We cannot overstate the strategic importance of incorporating both external and internal penetration testing into your cybersecurity strategy. Here’s a breakdown of why each type is critical and how they complement each other:
- Minimizing Impact and Enhancing Recovery:
- Regular internal and external penetration testing helps minimize the impact of an attack by enabling swift incident reporting, system cleanup, and business operation resumption.
- Provides a comprehensive security approach, identifying weak links and opportunities for unauthorized access.
- Compliance and Data Protection:
- Aids in compliance with industry regulations, thereby enhancing overall data protection measures.
- Regular testing ensures security measures remain effective against evolving cyber threats, safeguarding critical assets.
- Realistic Security Assessment:
- Offers a realistic assessment of the security posture by simulating real-world attack scenarios, identifying, and remediating potential vulnerabilities.
- Detailed post-testing reports outline vulnerabilities, risks, exploitation difficulty, and swift remediation recommendations.
Annual internal and external penetration tests help organizations identify vulnerabilities and enhance security policies, crucial for staying ahead of cyber threats and bolstering defenses against all actors.
Conclusion
Understanding the distinct methodologies and scopes of both external vs internal penetration testing strengthens cybersecurity defenses against various digital threats. Implementing both practices ensures a comprehensive security assessment, minimizing vulnerabilities from both outside attackers and potential internal threats.
In a landscape where cyber threats are constantly evolving, it’s critical to remain proactive in identifying and remediating vulnerabilities. Through regular penetration testing insights and recommendations, businesses can protect vital assets and meet industry regulations. For further information or to strengthen your cybersecurity framework through professional external and internal penetration testing, feel free to contact us. This dual-focused approach is not only strategic but essential for those aiming to maintain an edge over potential cyber adversaries.
Also learn what Data Privacy Here🔗
FAQs
Q: What is the difference between External vs Internal penetration tests?
To illustrate the contrast between External vs Internal Pentesting, insiders with privileged access, such as malicious employees or business partners, may exploit the vulnerabilities that internal penetration tests aim to uncover. In contrast, external penetration tests focus on identifying security weaknesses that outside attackers could exploit.
Q: What are the pros and cons of employing external versus internal penetration testers?
The main disadvantage of relying solely on internal testers is that they may have limited visibility of external threats. While they are effective at uncovering insider threats, they might not be able to detect vulnerabilities that are only apparent to external attackers.
Q: What aspects are common to both external and internal penetration testing?
The common element in both internal and external penetration testing is the target; both types of testing aim to secure the same systems and networks. However, internal attackers can be more devastating due to their in-depth knowledge of which systems are critical and their locations within the network.
Q: Can you explain what an internal penetration test entails?
An internal penetration test involves simulating the actions of a threat actor with internal access to determine how they might exploit network vulnerabilities. An insider could potentially compromise what sensitive information this type of test seeks to understand.
We trust this article effectively clarifies the disparities between External vs Internal pentesting and their respective requirements. Should you have further questions about External vs Internal pentesting, please do not hesitate to reach out to us.