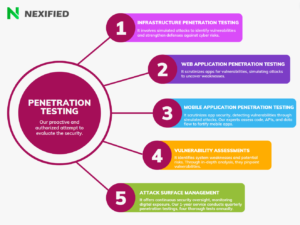
With healthcare organizations increasingly becoming targets for cybercriminals, the importance of healthcare cybersecurity has never been more pronounced. The rise in healthcare cyber attacks is driven by the vast amounts of personal and medical data contained within healthcare records, compounded by outdated legacy systems and the intricate networks that are characteristic of the healthcare sector.

In response to these challenges, establishing a comprehensive healthcare IT security strategy is crucial for safeguarding sensitive information and ensuring the continuity of healthcare operations. Strategies encompassing regular risk assessments, robust employee training, and effective incident response plans are essential in mitigating the risk of cyber attacks in healthcare, including the prevalent threat of hospital ransomware.
The Evolving Threat Landscape in Healthcare Cybersecurity
The healthcare sector has witnessed a significant evolution in cybersecurity threats, with an alarming increase in both the complexity and frequency of attacks. This trend underscores the urgent need for robust security measures to protect sensitive patient data and healthcare operations.
Specialized Assets and Common Threats
- Hospital Information Systems and IoT Devices: These critical assets streamline operations but also present attractive targets for cybercriminals.
- Phishing Attacks: Often initiating serious security breaches, these are typically designed to steal sensitive data through deceptive emails and messages.
- Ransomware: This type of malware encrypts valuable digital files and demands a ransom for their release, severely impacting healthcare services.
Impact of Cybersecurity Incidents
- Extended Care Disruptions: Cyber incidents can lead to significant delays in patient care and may force healthcare providers to divert patients to other facilities.
- Data Breaches and Financial Losses: The loss of access to medical records or financial data can have devastating consequences for both patients and healthcare organizations.
- Operational and Capacity Strain: Attacks may result in the cancellation of scheduled procedures and strain the provisioning of acute care.
Strategies and National Efforts
- National Cybersecurity Strategy: Initiatives like these aim to fortify the infrastructure against cyber threats through federal incentives and stricter accountability for data handlers.
- Employee Training and Awareness: Regular training sessions can significantly mitigate the risk posed by phishing and other socially engineered attacks.
Recent Trends and Statistics
- Increase in Cyber Attacks: Recent years have seen a surge in cyber incidents, with a notable rise in sophisticated ransomware attacks.
- Financial Implications: The cost associated with data breaches in healthcare has escalated, emphasizing the need for investment in cybersecurity measures.
The evolving threat landscape in healthcare cybersecurity demands continuous vigilance and adaptation of advanced security protocols to safeguard against potential cyber threats.
Key Components of a Robust Healthcare Cybersecurity Strategy
Adherence to Regulations and Comprehensive Policies
Healthcare cybersecurity strategies must align with stringent regulations such as HIPAA and HITECH. Developing comprehensive policies covering areas from incident response and access control to employee responsibilities and physical security is critical. These policies should be clear on expectations related to confidentiality, privacy, and security, and include procedures for regular risk assessments to identify potential vulnerabilities.
Multi-layered Security Measures and Regular Training
Implementing a multi-layered defense system is essential. This includes physical and technological safeguards like secure disposal, encryption at rest, and advanced security controls such as multi-factor authentication and network segmentation. Regular training programs that are engaging and tailored to address individual knowledge gaps play a crucial role in reinforcing security policies. These programs should include a variety of formats, from online modules to interactive workshops.
Integration of Advanced Technologies and Best Practices
Utilizing a consolidated security platform simplifies security management and enhances the effectiveness of cybersecurity measures. Regular updates and vulnerability patches are vital to maintain a robust defense against emerging threats. Best practices such as creating backups, encrypting sensitive data, and securing mobile devices must be rigorously followed to protect against data breaches and cyber attacks.
Proactive Incident Response and Business Continuity Planning
A proactive incident response plan and a comprehensive business continuity plan are indispensable components of a healthcare cybersecurity strategy. These plans ensure that healthcare operations can continue smoothly and reliably, even during a cyber incident, with strategies for data recovery, system restore, and maintaining hardware failover capabilities.
Continuous Improvement and Community Engagement
Cybersecurity is an evolving field that requires continuous improvement and adaptation. Healthcare organizations should engage with industry peers, cybersecurity experts, and government agencies to stay updated on new threats and solutions. Sharing knowledge and experiences about cybersecurity practices enhances the collective security posture of the healthcare sector.
Regulatory Compliance and Standards in Healthcare Cybersecurity
Navigating the complex landscape of regulatory compliance and standards is essential for maintaining robust healthcare cybersecurity. Healthcare organizations must adhere to a variety of regulations designed to protect patient data and ensure the integrity of healthcare IT systems.
Major Regulations Impacting Healthcare Cybersecurity
- Health Insurance Portability and Accountability Act (HIPAA): This critical U.S. legislation mandates the protection and confidential handling of protected health information (PHI).
- The General Data Protection Regulation (GDPR): For healthcare organizations operating in or dealing with the EU, GDPR imposes strict rules on data privacy and security, affecting how patient information is handled internationally.
- The Health Information Technology for Economic and Clinical Health (HITECH) Act: This act encourages the adoption of electronic health records in the U.S. and includes provisions for the privacy and security of patient data.
Compliance Frameworks and Certification Standards
- ISO/IEC 27001: Internationally recognized standard providing requirements for an information security management system (ISMS), helping organizations secure patient data.
- NIST Cybersecurity Framework: Offers a policy framework of computer security guidance for organizations in the healthcare sector to improve their ability to prevent, detect, and respond to cyber attacks.
Implementing Compliance in Healthcare Cybersecurity
Implementing these standards requires a structured approach:
- Assessment of Current Security Posture: Understanding current capabilities and gaps in compliance with healthcare cybersecurity regulations.
- Risk Management: Regular risk assessments to identify and mitigate potential vulnerabilities in healthcare systems and data protection measures.
- Employee Training and Awareness: Continuous education on regulatory requirements and cybersecurity best practices to ensure compliance and enhance security measures.
- Regular Auditing and Monitoring: Implementing ongoing auditing processes to ensure continuous compliance and adjusting strategies as regulatory landscapes evolve.
By integrating these compliance requirements into their cybersecurity strategies, healthcare organizations can not only fulfill legal obligations but also significantly enhance their overall security posture, protecting both patient data and critical healthcare infrastructure from cyber threats.
Fostering a Culture of Cybersecurity Awareness in Healthcare Organizations
Protecting Access and Privilege
Implementing adaptive multi-factor authentication and single sign-on, along with securing remote third-party access, are foundational measures in healthcare cybersecurity. These technologies help in safeguarding access to critical systems and sensitive data, thereby reducing the risk of unauthorized access.
Email Security and Phishing Defense
Given that email is a primary communication tool within healthcare organizations, it is also a significant vector for phishing attacks. Regular security awareness training is crucial to equip staff with the skills to recognize and thwart these threats. Ensuring that all personnel understand the signs of phishing can prevent potential breaches.
Physical and System Security
Securing physical devices is as important as cyber measures. This includes proper configuration and regular updates, especially for legacy systems that may lack security patches. Physical security measures prevent unauthorized access to critical infrastructure and help maintain system integrity.
Roles in Cybersecurity
Cybersecurity is a collective responsibility. Patients, workforce members, C-suite executives, and vendors all play roles. It’s vital that each group understands their part in protecting resources, with staff members serving as the first line of defense against breaches.
Celebrating Cybersecurity Efforts
Organizational celebrations of cybersecurity milestones and adherence to security practices foster a collaborative culture. These events reinforce the critical nature of everyone’s participation in cybersecurity efforts.
Leadership and Cybersecurity
Leadership is pivotal in driving a security-focused culture. Executives should actively support cybersecurity initiatives, communicate their importance, and model security best practices. By leading by example, leaders can instill a proactive security mindset throughout the organization.
Addressing Internal Risks
While external threats are often emphasized, internal risks must not be overlooked. Healthcare workers have access to extensive patient data and must be vigilant. Overcoming complacency and fostering an environment where staff regularly engage in security training and uphold accountability is essential.
By integrating these practices, healthcare organizations can foster a robust culture of cybersecurity awareness that not only enhances their defensive posture but also aligns with their overall strategic objectives in healthcare IT security.
Conclusion
Throughout this article, we’ve explored the multifaceted nature of healthcare cybersecurity, highlighting the increasing risks and outlining necessary strategies for bolstering defenses against cyber attacks. From understanding the evolving threat landscape to implementing robust security measures, continuous training, and regulatory compliance, the importance of a comprehensive cybersecurity framework within healthcare cannot be overstated. These efforts are essential not only for protecting sensitive patient data but also for ensuring the uninterrupted operation of healthcare services in the face of cyber threats.
As we move forward, it is clear that the journey to achieving and maintaining high levels of cybersecurity in healthcare is ongoing. The commitment to adopting advanced security technologies, fostering a culture of cybersecurity awareness, and engaging in continuous improvement and community collaboration will play pivotal roles in safeguarding the healthcare sector. By emphasizing the collective responsibility of protecting against cyber threats, healthcare organizations can better protect themselves and their patients from the potentially devastating impacts of cyber incidents.
Strengthen Healthcare Cybersecurity: Get Pentesting Services!
FAQs
What are the key components of cyber security? The five fundamental aspects of cyber security include:
- Confidentiality: Ensuring that information is accessible only to those authorized to have access.
- Integrity: Safeguarding the accuracy and completeness of information and processing methods.
- Availability: Ensuring that authorized users have access to information and associated assets when required.
- Authentication: Verifying the identity of users, systems, or entities before granting access to data.
- Non-Repudiation: Providing proof of the origin or delivery of data to protect against denial by one of the parties involved in a communication.
Can you explain what cyber security is and why it’s important?
Cyber security is a protective framework designed to shield networks, devices, and data from external threats. It is crucial for preserving the confidentiality of business information, sustaining employee productivity, and bolstering customer trust in a company’s products and services. Cyber security specialists are often employed by businesses to maintain this protective barrier.
What are the five critical requirements for cyber security according to the NIST Framework?
According to the NIST Cybersecurity Framework, businesses should focus on the following five functional areas:
- Identify: Catalog all hardware, software, and data, such as laptops, smartphones, tablets, and point-of-sale devices.
- Protect: Implement measures to ensure the safety of these assets.
- Detect: Develop capabilities to identify cybersecurity events promptly.
- Respond: Have a plan to address detected cybersecurity incidents.
- Recover: Establish strategies to restore any capabilities or services impaired due to a cybersecurity incident.
What are six important tips for maintaining cyber security awareness?
To maintain cyber security awareness, consider these six tips:
- Recognize that everyone is a potential target for hackers.
- Regularly update your software to mitigate vulnerabilities.
- Be vigilant against phishing scams and be cautious of suspicious emails and phone calls.
- Use strong password management practices.
- Exercise caution when clicking on links or downloading files.
- Never leave your devices unattended, as they could be compromised.
Learn what is [NIST Framework]